
‘Bring Your Own Device’ or BYOD is one of the best things to have happened to the enterprise work culture. Its features have been mutually beneficial to employees and employers alike.
While BYOD enables employees, especially remote workers, to work on the go, it has also proved to be a very cost-effective solution for employers. On average, BYOD helps enterprises save approximately $350 per year, per employee. But cost-effectiveness is only a secondary benefit of the BYOD culture. Its primary benefits for employers and employees include improved mobility, flexibility, and productivity.
However, implementing a BYOD culture is only half the work done. Its larger and exponential benefits can only be realized with a strategy that accounts for the multiple challenges that follow BYOD implementation. The primary among these includes:
- Securing Enterprise Apps.
- Accounting for Data and Security Risks.
- Accounting for Lost or Stolen Devices.
1. EMM for Securing Enterprise Apps
On average, an enterprise employee uses 5 business apps per day. A failure to manage even a single app may expose the corporate network to unforeseen security and data risks. A unified enterprise mobility management (EMM) solution equips enterprises with complete visibility of devices entering and exiting the corporate network. Further, it lends multiple other capabilities that are essential for seamless mobility governance and security.
- EMM helps enterprises efficiently manage third-party apps used by employees
- EMM offers enterprises the flexibility to add/remove remote workers on the go
- EMM allows enterprises with control to restrict employees from downloading apps that do not align with data and security policies.
2. MDM for Data and Security Risks
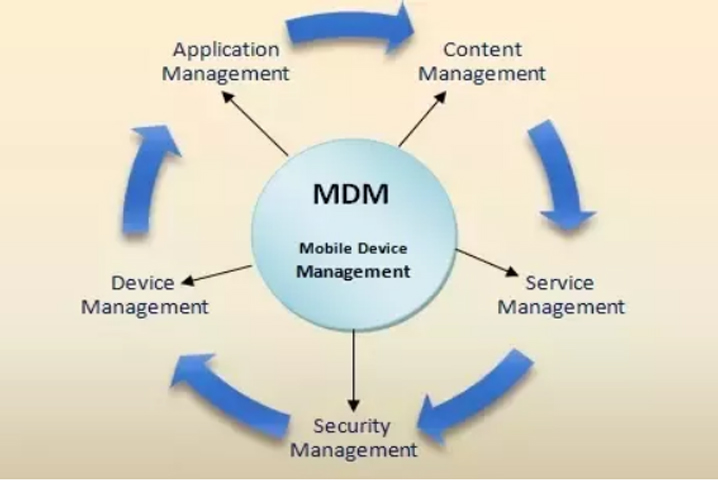
While mobility undoubtedly improves employee ease of doing work, the risks to critical business data multiply by manifold. Ideally, large enterprises prefer agent-based mobile device management (MDM) solutions for enforcing features such as password protection, remote data wiping, blocking unsafe WLAN networks, etc. Moreover, an MDM solution integrates easily in diverse environments with multiple types of mobile devices, overlapping workflows, etc.
3. Policy Enforcement For Lost or Stolen Devices
When devices part of a BYOD network are lost or stolen, it exposes business-critical data to an external party. Employees must be well educated in terms of BYOD policies, particularly policies related to theft or loss. An employee must notify such events at the earliest so the IT admin team can take all necessary steps to prevent organizational data from misuse.
4. Feature Update and Distribution
Employees keep changing their mobile devices. Moreover, enterprise workflows, functions, and employees are also constantly changing. Enterprises need to create a BYOD ecosystem which facilitates the following:
- Prevents data retention in case an employee changes his/her devices or leaves the job
- Allows easy updates and distribution of new features, policies, etc.
- Allows easy customization by grouping devices as per department, job functions, security settings, etc.
BYOD is the future of business. But to create a secure BYOD environment, an enterprise must invest in fine-tuning the capabilities of its IT Team. Moreover, security is not the responsibility of the employer alone. Employees too need to be aware of all BYOD policies and must do everything necessary to enforce them.
True benefits of BYOD are possible if and only if employers and employees are in conjunction with one another. Pratham Software has been the preferred choice for global enterprises to implement a safe BYOD environment. Our MDM and EMM solutions are designed to serve specific requirements while addressing all security risks that come with enterprise mobility solutions.








